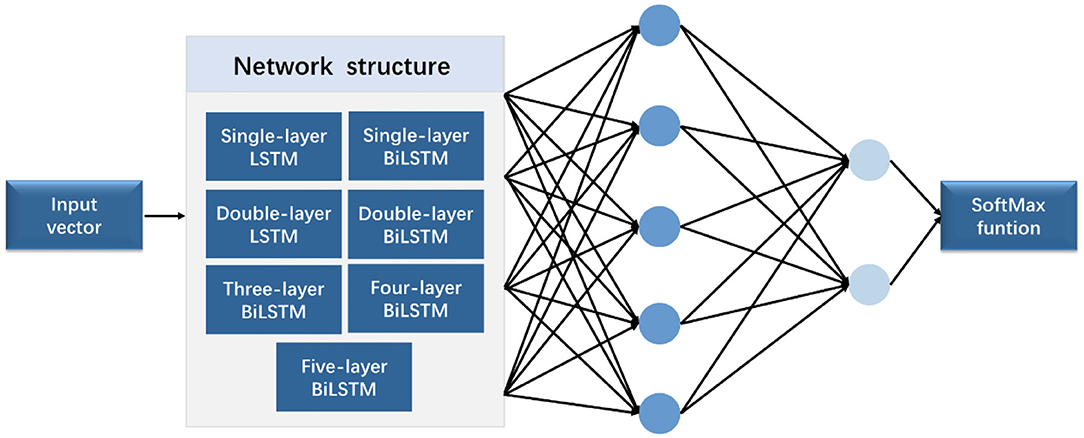
41 based on the diagram which network line code technique is being used
Modem: What is a Modem? Types of Modems - Computer Notes • The line interface of the modem can have a 2-wire or a 4-wire connection to transmission medium. 4-wire Modem • In a 4-wire connection, one pair of wires is used for the outgoing carrier and the other pair is used for incoming carrier. • Full duplex and half duplex modes of data transmission are possible on a 4- wire connection. PDF Calculating Critical Path & Float for a Network Diagram Step 1: Draw a Network Diagram Task 1, 4 days Task 2, 5 days Task 3, 3 days Task 4, 7 days Task 5, 4 days 0 4 4 9 14 18 4 7 147 Task 5 is dependent on Task 2 and Task 4 being complete. So, ES for Task 5 is 14 days (dependent on Task 4, which is the longer task. For forward pass, calculate the Early Start (ES) and Early Finish (EF).
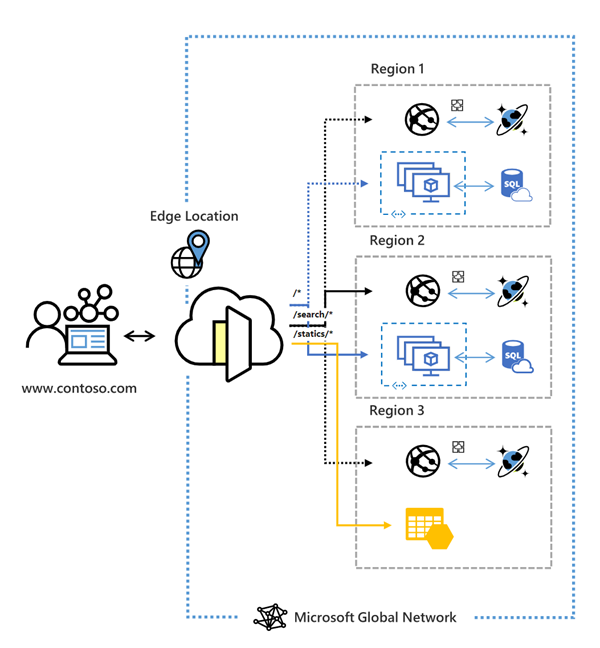
PDF Design Standards Electrical Schematic Diagrams Note: Equipment codes shorter than 5 chars/digits shall be completed with underscores (_). 6.2 DIAGRAMS PRODUCED BY ST/CV The position normally used for the equipment code is replaced by a 1 character system code followed by a 4 digit building number. The structure of the drawing number is: Project code: A project identification code.
Based on the diagram which network line code technique is being used
Network Diagram Guide: Learn How to Draw Network Diagrams ... It is used in the network diagram (usually represented by a dotted arrow) to show dependency or connectivity between two or more activities. For example, A and B are concurrent. C is dependent on A; D is dependent on A and B. This relationship is shown with the help of the dotted arrow. Network Diagram Best Practices Testout Section 1.4.4 Flashcards - Quizlet Match the description on the left with the appropriate network signal line code on the right. Non-Return-to-Zero Binary 1s are represented by positive voltage while 0s are represented by negative voltage. There is no zero voltage state between bits. Manchester The transition from one voltage level to another is used to represent binary data Digital Communication - Line Codes - Tutorialspoint A line code is the code used for data transmission of a digital signal over a transmission line. This process of coding is chosen so as to avoid overlap and distortion of signal such as inter-symbol interference. Properties of Line Coding Following are the properties of line coding −
Based on the diagram which network line code technique is being used. Hamming Code - Error Detection and Error Correction ... First, we need to detect whether there are any errors in this received hamming code. Step 1: For checking parity bit P1, use check one and skip one method, which means, starting from P1 and then skip P2, take D3 then skip P4 then take D5, and then skip D6 and take D7, this way we will have the following bits, Testout Section 1.4 Flashcards - Quizlet Network Signaling is a function of which later of the OSI Model? ... Based on the diagram, which network line code technique is being used? Non-Return-to-Zero. THIS SET IS OFTEN IN FOLDERS WITH... Network Pro. 209 terms. Ben_Monday. Testout Network Pro 2.3.4. 9 terms ... Diagrams. Flashcards. Mobile. Help. Sign up. Help Center. Honor Code ... Digital Communication - Phase Shift Keying PSK technique is widely used for wireless LANs, bio-metric, contactless operations, along with RFID and Bluetooth communications. PSK is of two types, depending upon the phases the signal gets shifted. They are − Binary Phase Shift Keying B P S K This is also called as 2-phase PSK or Phase Reversal Keying. 17 Important Data Visualization Techniques | HBS Online Bullet Graph. Choropleth Map. Word Cloud. Network Diagram. Correlation Matrices. 1. Pie Chart. Pie charts are one of the most common and basic data visualization techniques, used across a wide range of applications. Pie charts are ideal for illustrating proportions, or part-to-whole comparisons.
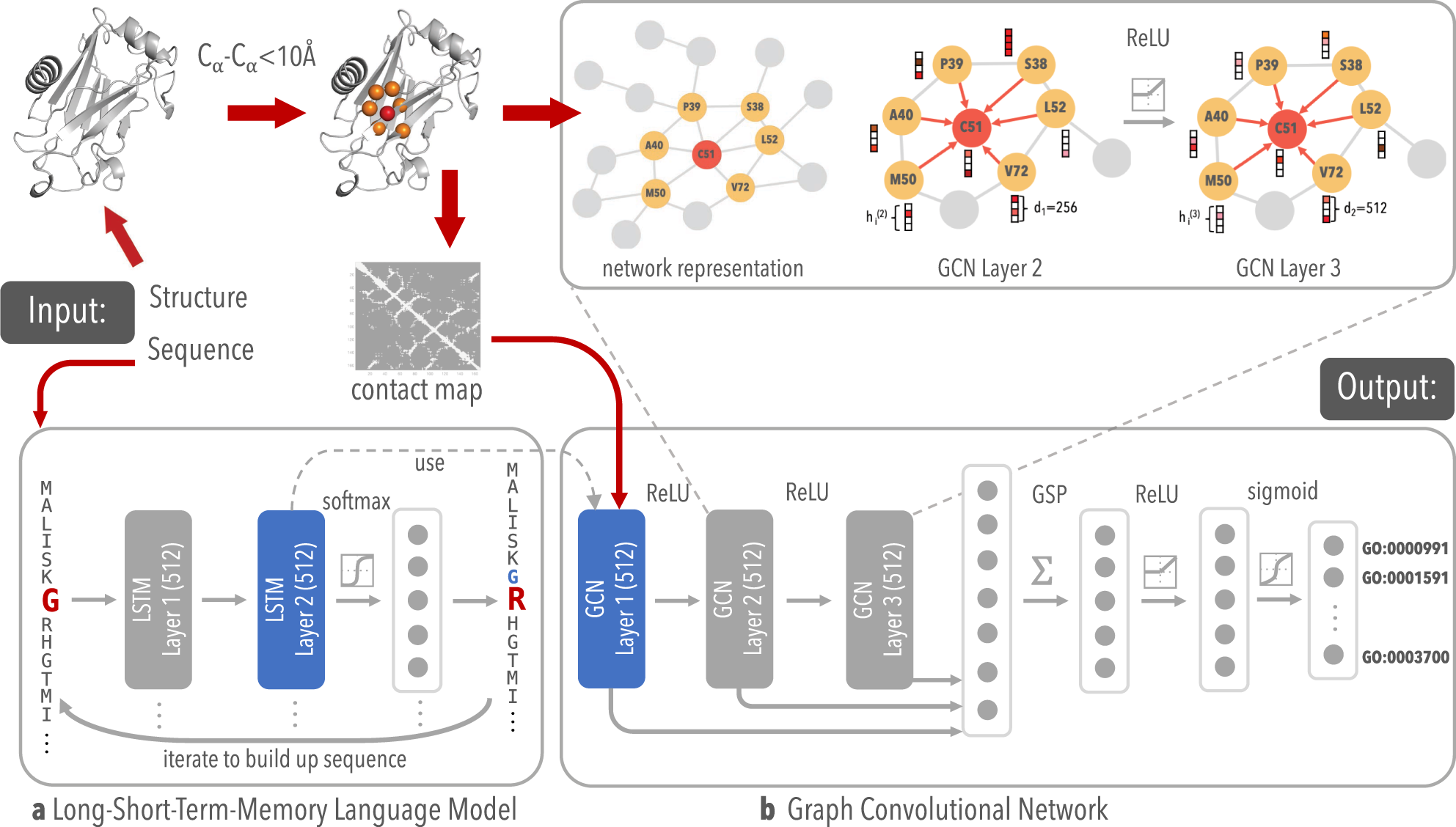
Image Compression: ML Techniques and Applications This method is the most capable at coding symbols based on the likelihood of their occurrence. 4. Entropy Encoding: This method reduces the size of the dataset necessary to deliver a certain quantity of data. In Huffman and arithmetic coding approaches, the entropy coding method is applied. What is a PERT Chart and How to Use it, With Examples PERT chart (Program Evaluation Review Technique): A PERT chart is a project management tool used to schedule, organize, and coordinate tasks within a project. PERT stands for Program Evaluation Review Technique , a methodology developed by the U.S. Navy in the 1950s to manage the Polaris submarine missile program. A similar methodology, the ... Difference between Unipolar, Polar and Bipolar Line Coding ... Manchester Encoding in Computer Network Let's experiment with Networking Layers of OSI Model TCP/IP Model Physical layer Network Devices (Hub, Repeater, Bridge, Switch, Router, Gateways and Brouter) Types of Transmission Media Transmission Modes in Computer Networks (Simplex, Half-Duplex and Full-Duplex) Analog to Digital Conversion PDF Design and UML Class Diagrams - University of Washington UML class diagrams • UML class diagram: a picture of -the classes in an OO system -their fields and methods -connections between the classes • that interact or inherit from each other • Notrepresented in a UML class diagram: -details of how the classes interact with each other -algorithmic details; how a particular behavior is ...
Multiplexing : Different Types, Advantages & Applications Muxing (or) multiplexing can be defined as; it is a way of transmitting various signals over a media or single line. A common kind of multiplexing merges a number of low-speed signals to send over an only high-speed link, or it is used to transmit a medium as well as its link with a number of devices. It provides both privacy & Efficiency. Manchester Encoding in Computer Network - GeeksforGeeks Manchester Encoding in Computer Network Let's experiment with Networking Layers of OSI Model TCP/IP Model Physical layer Network Devices (Hub, Repeater, Bridge, Switch, Router, Gateways and Brouter) Types of Transmission Media Transmission Modes in Computer Networks (Simplex, Half-Duplex and Full-Duplex) Analog to Digital Conversion Enhancing software model encoding for feature location ... Door control development can be broken down into: (1) finding a model fragment similar to the one you want to develop and (2) modifying it based on new requirements. Since the company's models are unknown to the engineer, locating or identifying a similar fragment will be like looking for a needle in a haystack. Precedence Diagramming Method (Activity on Node Method) in ... A Precedence Diagramming Method (PDM) or Activity on Node (AON) diagramming method is a graphical representation technique. It shows the interdependencies of activities and is used in schedule development. We use this method to draw the project schedule network diagrams, such as critical path network, critical chain network diagram, and others.
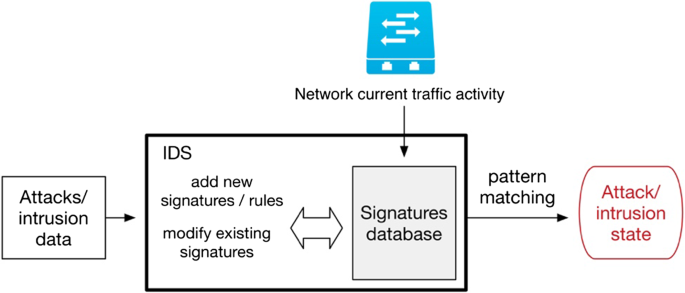
Network Based Intrusion Detection System - an overview ... Network-based intrusion detection systems (NIDS) are devices intelligently distributed within networks that passively inspect traffic traversing the devices on which they sit. NIDS can be hardware or software-based systems and, depending on the manufacturer of the system, can attach to various network mediums such as Ethernet, FDDI, and others.
PDF FIBER OPTIC COMMUNICATIONS - University of Texas at Dallas mBnB Line Codes mBnB -codes m binary bits into n bits (m
Network - K-Line - Pico auto The K-Line is a very low-speed single-wire serial communication system used on many motor vehicles and commercial vehicles. It is commonly used for the diagnostic connections between the Electronic Control Modules (ECMs) on the vehicle and the diagnostic equipment (scan tools and data loggers). The K-Line is a network based upon the ISO9141 ...
Telecom Testout Study Guide Flashcards - Quizlet Configures the switch to obtain an IP address from a DHCP server. You are configuring a switch so that you can manage it via PuTTY from the same network segment as the switch. On the switch, you enter the following commands: switch#config terminal switch (config)#interface vlan 1 switch (config-if)#ip address 192.168.1.10 255.255.255.
6 Types of Artificial Neural Networks Currently Being Used ... This paper explains the usage of Feed Forward Neural Network. The X-Ray image fusion is a process of overlaying two or more images based on the edges. Here is a visual description. 2. Radial basis function Neural Network: Radial basic functions consider the distance of a point with respect to the center.
Multiplexing - What is Multiplexing ?Explain its ... Multiplexing or (muxing) - To combine multiple signals (analog or digital) for transmission over a single line or media. A common type of multiplexing combines several low-speed signals for transmission over a single high-speed connection. In other words, we can say that Muxing used for sharing of a medium and its link by two or more devices.
PEN Testing Final Flashcards - Quizlet Examine the following network diagram. What is the most appropriate location for a web application firewall (WAF) on this network? ... What technique is being used in the following command: host -t axfr domain.com dns1.domain.com. ... Examine the following line of code. In what programming language is it written?
Networking 1 -BT Quiz/Test | Computer Science Flashcards ... Based on the diagram, which network line code technique is being used? Non-Return-To-Zero Which protocol is used on the World Wide Web to transmit Web pages to Web browsers? HTTP Which TCP/IP protocol will enable messages to be exchanged between systems? SMTP Which TCP/IP protocol would you implement that provides this capability? TCP
Line Coding in Digital Communication - Fosco Connect In telecommunication, a line code (also called digital baseband modulation, also called digital baseband transmission method) is a code chosen for use within a communications system for baseband transmission purposes. Line coding is often used for digital data transport.
Network Address Translation (NAT ... - GeeksforGeeks Network Address Translation (NAT) is a process in which one or more local IP address is translated into one or more Global IP address and vice versa in order to provide Internet access to the local hosts. Also, it does the translation of port numbers i.e. masks the port number of the host with another port number, in the packet that will be ...
Digital Communication - Line Codes - Tutorialspoint A line code is the code used for data transmission of a digital signal over a transmission line. This process of coding is chosen so as to avoid overlap and distortion of signal such as inter-symbol interference. Properties of Line Coding Following are the properties of line coding −
Testout Section 1.4.4 Flashcards - Quizlet Match the description on the left with the appropriate network signal line code on the right. Non-Return-to-Zero Binary 1s are represented by positive voltage while 0s are represented by negative voltage. There is no zero voltage state between bits. Manchester The transition from one voltage level to another is used to represent binary data
Network Diagram Guide: Learn How to Draw Network Diagrams ... It is used in the network diagram (usually represented by a dotted arrow) to show dependency or connectivity between two or more activities. For example, A and B are concurrent. C is dependent on A; D is dependent on A and B. This relationship is shown with the help of the dotted arrow. Network Diagram Best Practices

















0 Response to "41 based on the diagram which network line code technique is being used"
Post a Comment